When beginners start learning ethical hacking or bug bounty hunting, they often assume they need complex tools like Burp Suite, Kali Linux, or advanced scanners. The truth is far simpler and much more encouraging. Many high-severity vulnerabilities can be found using nothing but your web browser. Chrome DevTools alone gives you the power to inspect requests, analyze APIs, alter parameters, identify hidden functionality, and even detect broken access control.
This browser-only approach is not just convenient. It helps you master the fundamentals of web application security, something every professional bug bounty hunter values. This article will guide you through a complete workflow to turn your browser into a fully functional hacking lab, helping you uncover real vulnerabilities while building strong core skills.
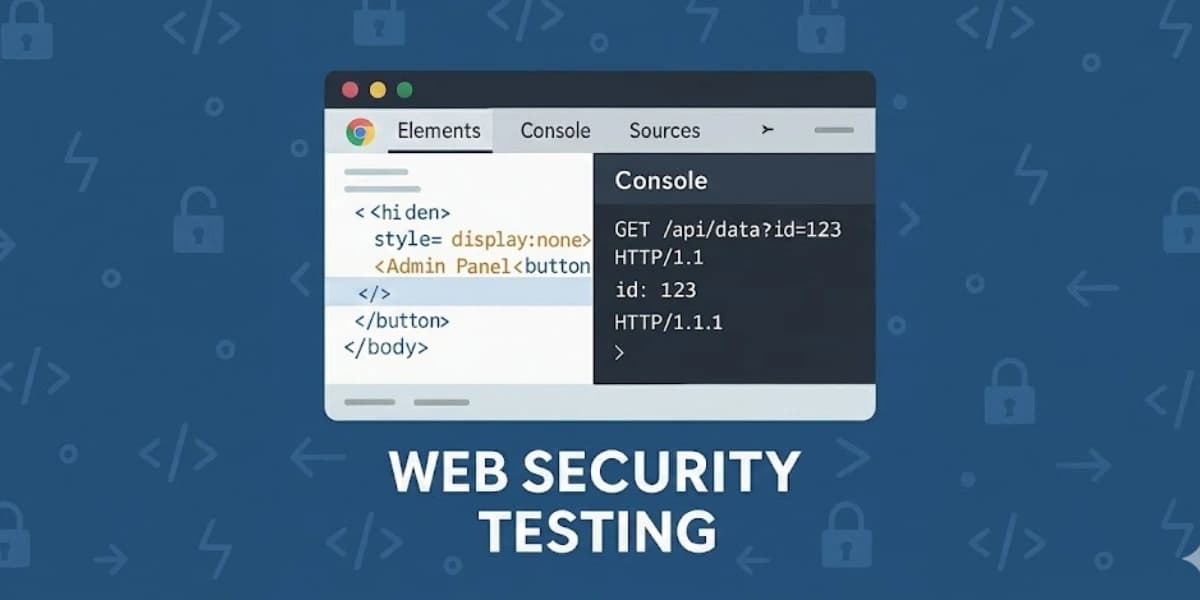
The Browser: An Overlooked but Powerful Ethical Hacking Tool
Every website you use is constantly sending and receiving data through your browser. Each login attempt, each button click, each form submission triggers a request behind the scenes. Your browser already has everything it needs to show you how these interactions work—it simply needs you to open DevTools.
This is why browser-based hacking is so effective. It doesn’t hide anything behind a tool. You are forced to understand how the application behaves. You learn how HTTP requests, API endpoints, authentication tokens, and frontend logic all connect. This knowledge stays with you long after you move on to advanced tools, and it makes you far better at identifying vulnerabilities that scanners cannot detect.
Inspect Element: Discovering Hidden Frontend Functionality
The Elements tab in DevTools is the simplest yet most revealing area for beginners. It lets you view and modify the HTML structure of a web page in real time. Many vulnerabilities begin with something as simple as a “hidden” or “disabled” button.
For instance, a website might visually hide an admin panel using CSS:
<div style="display:none">Admin Dashboard</div>
Removing that style suddenly exposes functionality that should never be accessible to normal users. This alone has led to real bug bounty payouts.
Disabled buttons create similar opportunities. Developers may disable a destructive feature—like deleting an account—through the frontend, but if they forget to enforce server-side authorization, removing the disabled attribute allows the action to run anyway.
Hidden form inputs also deserve attention. They often contain sensitive values such as user roles, pricing information, or flags that determine access levels. Changing these values allows you to test whether the server is validating them or simply trusting the browser.
In short, “Inspect Element” helps you uncover vulnerabilities related to:
- Hidden functionality
- Disabled buttons
- Client-side role enforcement
- Manipulated form values
- Broken access control
These are simple concepts, but they form the foundation of many real-world bug reports.
Network Tab: Your Gateway to Understanding Backend Behavior
The Network tab is the heart of browser-based ethical hacking. It reveals every request your browser sends and every response it receives, allowing you to understand the full communication flow of the web application. If your goal is to become a good bug bounty hunter, this is where you should spend most of your time.
As you interact with the website, watch for patterns:
- Which endpoints are being called?
- What parameters are included in requests?
- Are any admin or internal APIs visible?
- Does the server return more data than it should?
A very common bug is when an API returns all user records even though the interface displays only a limited number. This results in unintentional data exposure. Similarly, you may find endpoints with “admin”, “debug”, or “export” in their path. Sometimes, these endpoints lack proper authentication or return sensitive information through poorly implemented access controls.
The Network tab also helps identify IDOR (Insecure Direct Object Reference) vulnerabilities. If changing a user ID in a request allows you to view or modify someone else’s data, you’ve discovered a serious flaw.
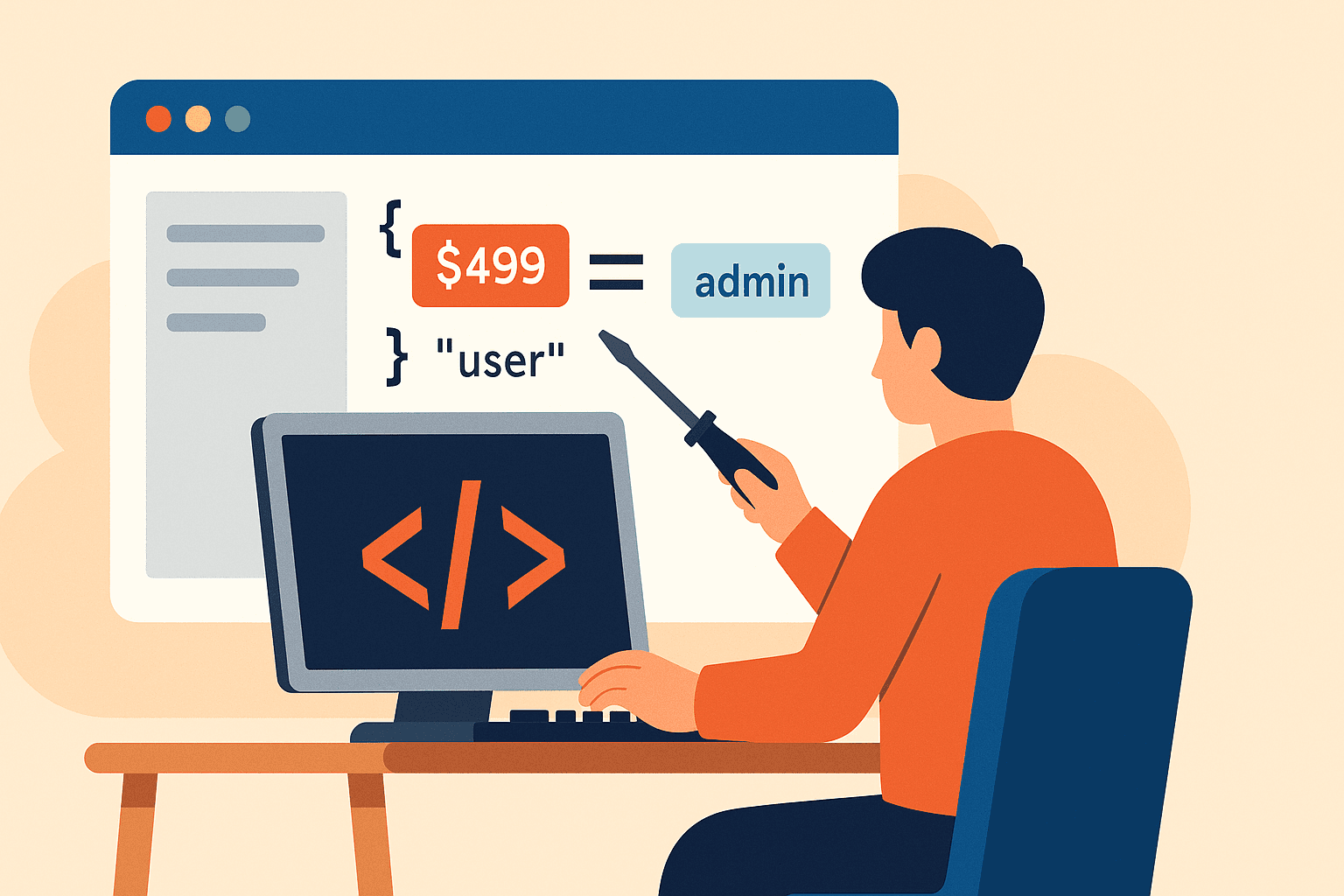
Parameter Tampering: Testing the Trust Between Browser and Server
Parameter tampering is where browser-only hacking becomes extremely powerful. Most applications send important values from the frontend to the backend, and it is surprisingly common for developers to assume these values will never be changed by the user.
This creates a perfect scenario for ethical hackers. Using DevTools, you can intercept requests, edit the values, and send them again to the server.
Here are a few high-impact values to test:
- Prices (“price=499” → “price=1”)
- User roles (“role=user” → “admin”)
- Account IDs (switching one ID to another)
- Boolean flags (“isPremium:false” → “true”)
- Quantity or limits (“limit=10” → “limit=1000”)
If the server accepts your modified request without proper validation, you’ve uncovered a major vulnerability. Many bug bounty programs reward parameter tampering discoveries because they represent real security failures that can lead to privilege escalation or financial loss.
This technique is especially important for learning manual testing—the essential skill that separates beginners from experienced security researchers.
Application Tab: Investigating Cookies, Storage, and JWT Tokens
The Application tab is often overlooked but holds enormous potential for vulnerability discovery. Here, you can view everything stored on the client side, including cookies, session tokens, JWTs, and localStorage data.
Many developers store sensitive information directly in localStorage, assuming users will never inspect it. But DevTools shows you exactly what’s there, and sometimes it includes:
- Authentication tokens
- User roles
- API keys
- Feature flags
- Debugging information
JWT manipulation is particularly powerful. If a token includes claims like "role": "user" and the backend does not verify its signature correctly, modifying that value to "admin" may allow unauthorized access. Such flaws have led to bug bounty rewards ranging from a few hundred to several thousand dollars.
Checking cookies is equally important. Poorly configured session cookies can expose users to session hijacking, CSRF vulnerabilities, or insecure authentication flows.
Reverse Engineering JavaScript: Learning the Logic Behind the Site
JavaScript files often reveal far more than developers expect. By browsing through them in the “Sources” tab, you may find clues about how certain features work, what routes are available, or how role checks are handled. Sometimes, developers leave important comments, debug statements, or unused functions that inadvertently expose sensitive information. Looking inside JavaScript gives you a deeper understanding of the application’s internal logic. This knowledge not only helps you spot vulnerabilities but also improves your intuition when analyzing any future web application.
Why Browser-Based Hacking Creates Better Security Professionals
The biggest advantage of browser-based hacking is that it forces you to think. Tools automate tasks, but they don’t teach you why something is insecure. When you manually inspect an API request or watch how a page loads data, you begin to understand the relationships between frontend behavior and backend logic.
This is the mindset that helps you find logical vulnerabilities—issues scanners almost never catch. In bug bounty programs, these logical bugs often lead to the highest payouts, making manual browser-based testing one of the most valuable skills you can develop early in your journey.
Final Thoughts
Your browser is not just a tool for browsing the web. It is a powerful, fully capable hacking environment that allows you to inspect, modify, and understand web applications at a deep level. Using Chrome DevTools alone, you can detect broken access control, IDOR vulnerabilities, insecure API design, JWT misconfigurations, and poorly implemented frontend logic.
If you build these core skills through manual testing, you will be far better prepared for advanced tools and techniques later. And more importantly, you’ll develop the mindset needed to become a successful ethical hacker or bug bounty hunter.

