Introduction
Most beginners assume that critical security vulnerabilities appear as obvious failures like a login bypass, a major SQL injection, or an exposed admin panel. In real-world applications, this rarely happens. The most serious vulnerabilities usually begin quietly and go unnoticed at first. They often start with small, easily ignored details such as an unusual parameter, an API response that reveals more data than expected, or a feature that behaves differently under specific conditions. Individually, these issues may not look dangerous. They are not vulnerabilities by themselves. They are observations. In bug bounty hunting and real-world security testing, these small observations are what lead to high-impact findings, making them far more powerful than chasing obvious exploits.
Why Critical Vulnerabilities Rarely Appear Obvious
Applications today are large, layered, and complex. They are built using multiple moving parts, including:
- Frontend frameworks
- Backend APIs
- Authentication services
- Third-party integrations
Because of this architecture, security failures rarely occur in a single place. Instead, they happen between components. One developer assumes another layer will handle security, another layer assumes validation has already been performed, and no one reviews the entire flow end to end. This creates gaps. A critical vulnerability is usually not the result of one obvious mistake but the outcome of small gaps aligning together, and that alignment is exactly what attackers look for.
Observation Is a Skill, Not a Tool
Many people confuse observation with scanning, but they are not the same. Scanning usually means running tools and waiting for automated output, while observation means actively watching how an application behaves and thinking about what you see. Observation involves:
- Using the application normally
- Comparing expected behavior with actual behavior
- Paying attention to details that feel inconsistent
This is why experienced bug hunters often find vulnerabilities without using advanced payloads or complex tools. They succeed because they notice what others skip.
A Simple Rule: If Something Feels Odd, It Probably Matters
One of the most important mental rules in bug bounty is this:
If something feels slightly wrong, do not ignore it.
Beginners often ignore small details because they seem harmless, while professionals investigate them because unusual behavior rarely exists without a reason. An odd behavior does not guarantee the presence of a vulnerability, but ignoring it guarantees that you will never find one.
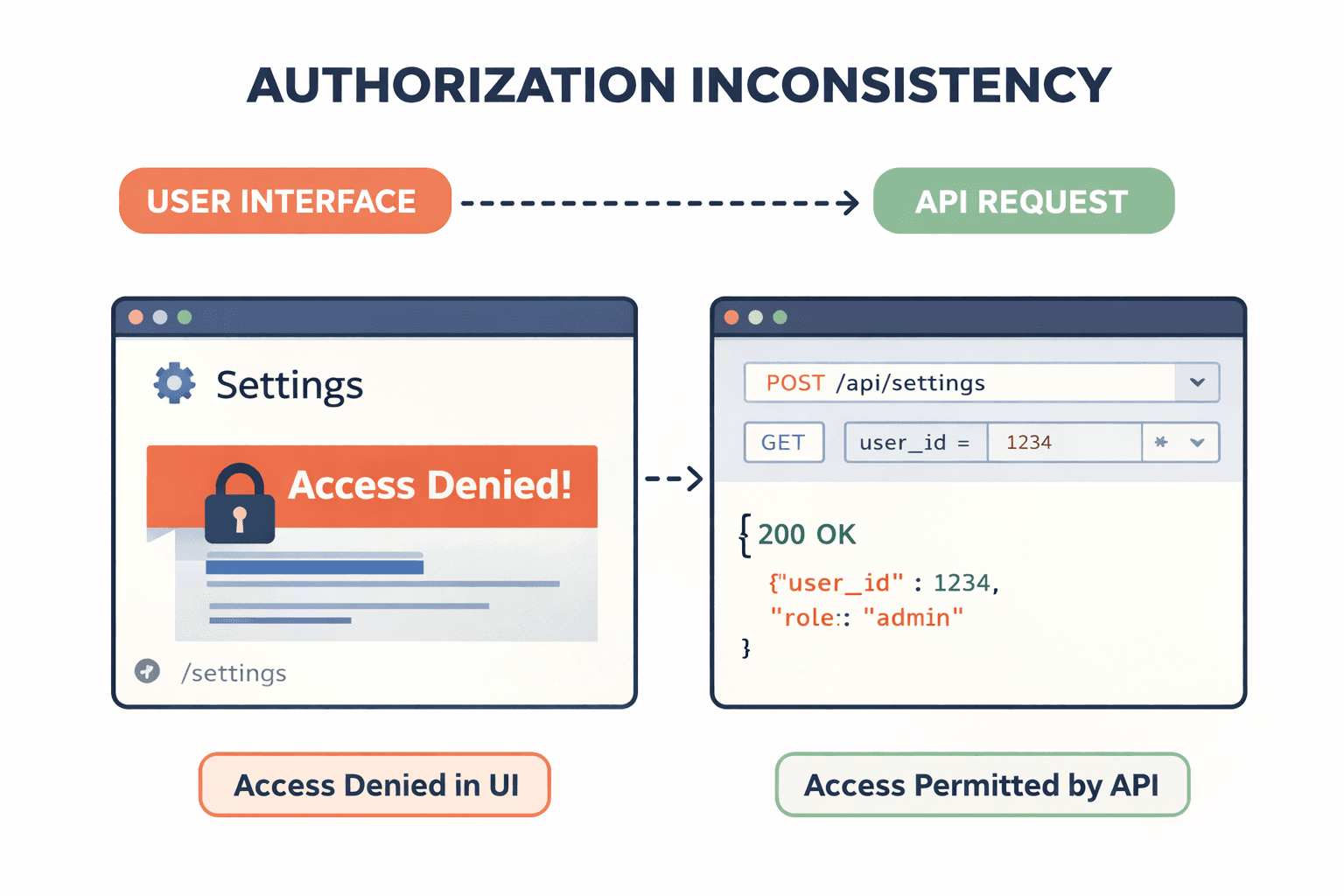
Small Observation #1: Inconsistent Authorization Behavior
Authorization issues are responsible for some of the most severe security vulnerabilities, yet they rarely appear as obvious access bypasses. Instead, you might notice small details such as a button being hidden for normal users while the API endpoint still responds when accessed directly. At first, this may look like nothing. However, that single observation raises important questions:
- Is authorization enforced on the server side?
- Are user roles validated for every request?
- Can object identifiers be modified?
This is how IDOR and privilege escalation vulnerabilities are usually discovered. The vulnerability itself was not immediately visible. The inconsistency was.
Small Observation #2: Predictable or Exposed Identifiers
Identifiers are everywhere:
- User IDs
- Order IDs
- Ticket numbers
- File references
You observe:
- IDs increment sequentially
- IDs appear in URLs or API responses
- IDs are reused across endpoints
On its own, this is not a vulnerability.
But it becomes one when:
- Authorization checks are missing
- Ownership is not validated
- Backend trusts the client
Many critical data exposure bugs start with noticing a simple number pattern.
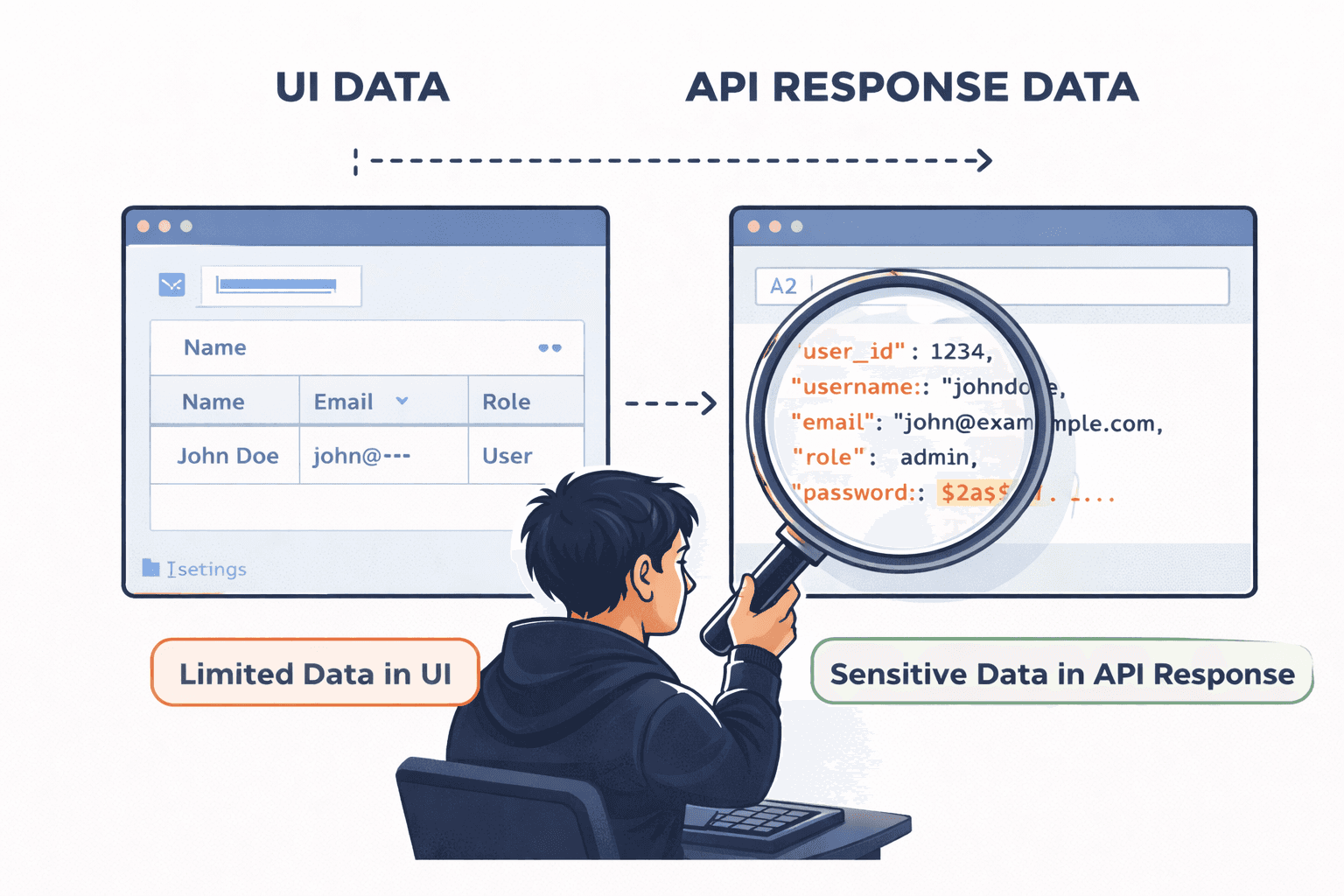
Small Observation #3: Extra Fields in API Responses
Modern frontends often consume large API responses, and developers sometimes return full objects while relying on the UI to display only the required fields. In such cases, you may observe that the interface shows limited data while the API response itself contains sensitive fields. This is a clear red flag. That observation should immediately raise important questions:
- Who is allowed to access this endpoint?
- Is data filtering handled on the server side?
- Are these sensitive fields exposed to other users?
Following this line of thinking often leads to serious findings such as sensitive information disclosure, account data leakage, and critical business logic flaws.
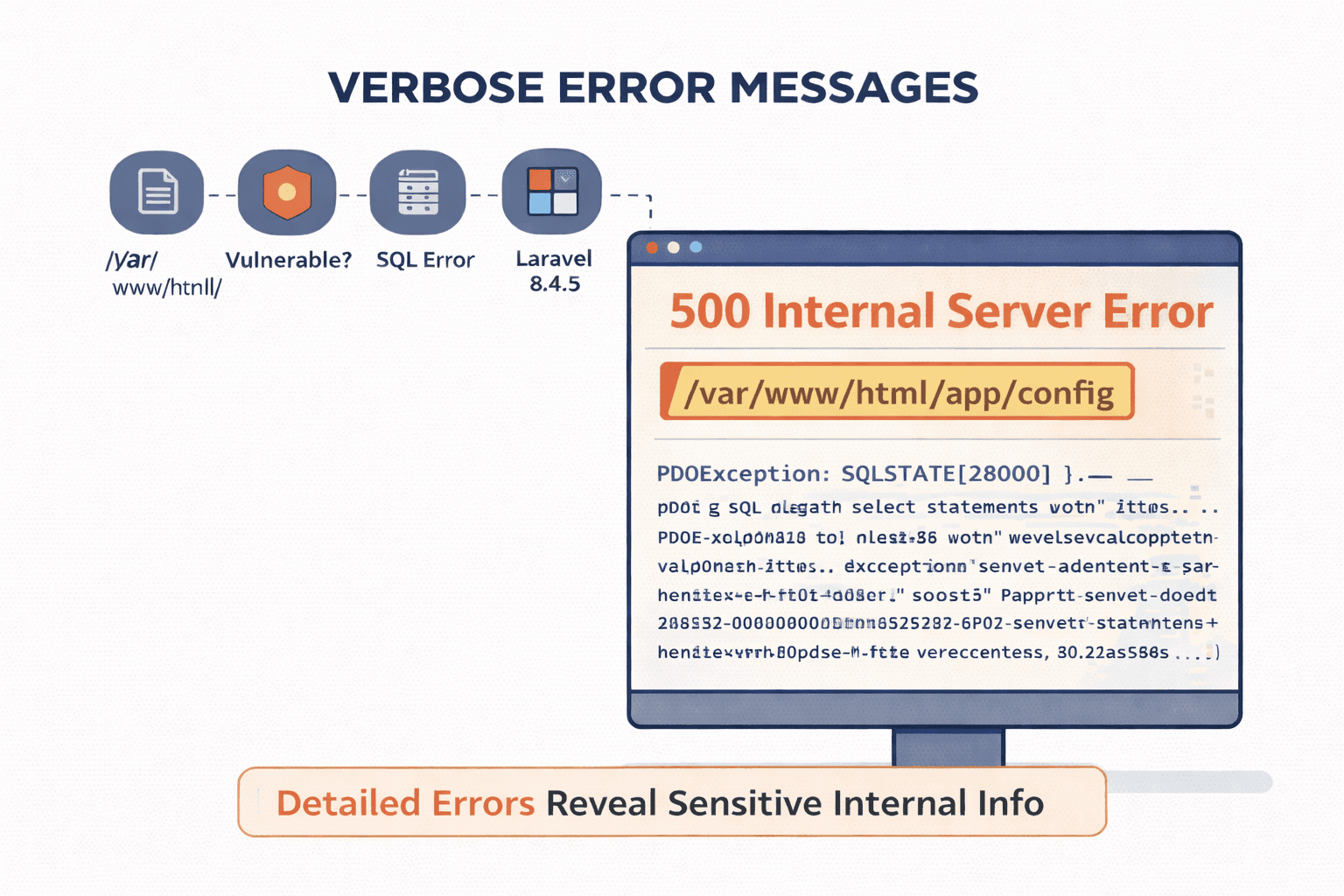
Small Observation #4: Verbose Errors and Debug Behavior
Error messages are often underestimated.
You observe:
- Detailed stack traces
- File paths
- Database errors
- Debug messages in production
One error message is rarely critical. But error messages reveal how the application thinks.
They expose:
- Internal structure
- Technology stack
- Validation logic
When combined with other observations, error messages help attackers move with confidence instead of guessing.
Note: Information disclosure bugs are rarely dangerous alone, but they dramatically increase the success rate of other attacks.
Small Observation #5: Feature Abuse Instead of Exploitation
Some of the highest impact bugs involve no technical exploitation at all. Instead, you may observe behaviors such as a coupon being reused, a refund being triggered repeatedly, or a limit being bypassed simply by changing the order of requests. Nothing crashes and no payloads are injected. The application behaves exactly as it was coded, but not as it was intended to work. This is a business logic failure. The vulnerability exists because developers assume users will behave honestly. Attackers do not.
Why Most Bug Hunters Miss These Details
There are consistent reasons why small observations are ignored.
Tool Dependence
Many beginners believe that tools will reveal everything. In reality, tools are designed to detect known patterns. They do not understand application logic, intent, or context.
Speed Over Understanding
People rush:
- Scan quickly
- Test payloads
- Move on
Observation requires patience.
Fear of “Low Severity”
Many hunters stop investigating when something looks purely informational. They forget that informational findings often become critical when they are chained together.
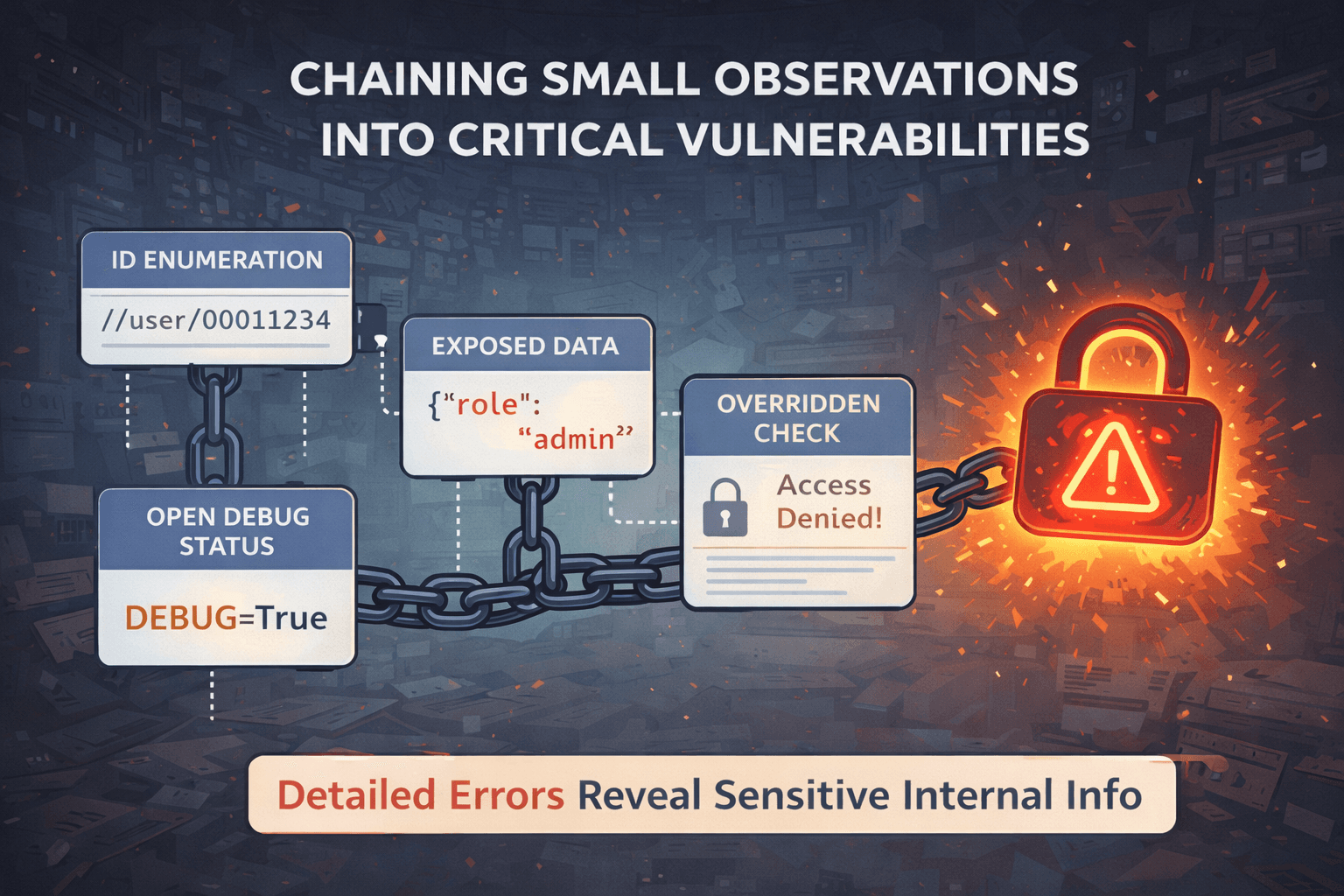
Chaining: Where Observations Become Critical
A single observation is rarely enough to create real impact. Serious vulnerabilities usually emerge through chaining.
Example:
Extra API data observed
Predictable IDs noticed
Missing authorization discovered
Data of other users accessed
Each step alone may look minor. Together, they result in full account compromise. This is why strong vulnerability reports focus on explaining the journey, not just the final exploit.
How to Train Yourself to Observe Better
Observation improves with deliberate practice.
Slow Down Application Usage
Use features like a normal user before testing them like an attacker.
Compare User Roles
Observe how behavior changes between accounts.
Watch Network Traffic Carefully
Look for unused parameters and unexpected responses.
Break One Assumption at a Time
Do not test everything at once. Change one variable.
Take Notes
Small details matter later when connecting dots.
If you do not document observations, you will forget the ones that matter most.
Why Observation Beats Payload Knowledge
Payloads change. Tools evolve. Frameworks update.
But human assumptions remain.
Every application assumes something:
- Users will not manipulate requests
- Clients will enforce rules
- Features will not be abused
Observation targets assumptions. That is why hunters with fewer tools but sharper observation often outperform others.
The Modern Attack Surface Makes Observation Even More Important
Applications today include:
- Mobile apps
- Public APIs
- Private APIs
- Third-party services
This increases complexity, and complexity increases inconsistency. Observation allows you to see where different components disagree with each other, and that disagreement is exactly where vulnerabilities live.
Final Thoughts
Critical vulnerabilities rarely come from brilliance or complex techniques. They come from attention and patience. They are discovered by noticing details that most people overlook, asking questions when others are satisfied with surface-level answers, and treating small inconsistencies as meaningful signals rather than background noise. Skilled bug hunters do not rush to exploit. They slow down, observe, and try to understand how the application truly behaves under different conditions.
If you want to improve your bug bounty results, stop chasing massive, obvious flaws that everyone else is scanning for. Start paying close attention to the small things: subtle behavior changes, unexpected responses, and assumptions made by the application. These small observations may seem insignificant on their own, but over time they connect and reveal deeper issues. In real-world security, small observations are the seeds from which critical vulnerabilities grow.

